This is a write up for the tryhackme room Pickle Rick
This Rick and Morty themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
Enumeration
First step, to enumerate the target machine and see what ports and service is running we use nmap .
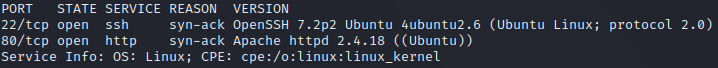
So there are an http service running in port 80 and a ssh service running in port 22. The information given in the introduction tells us to focus on the webserver.
We navigate to the given IP and see a static webpage. If we look at the source code
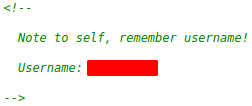
We got a username. Next we are going to use gobuster to scan the web site and see if there is some place we can use this username, or get more info.
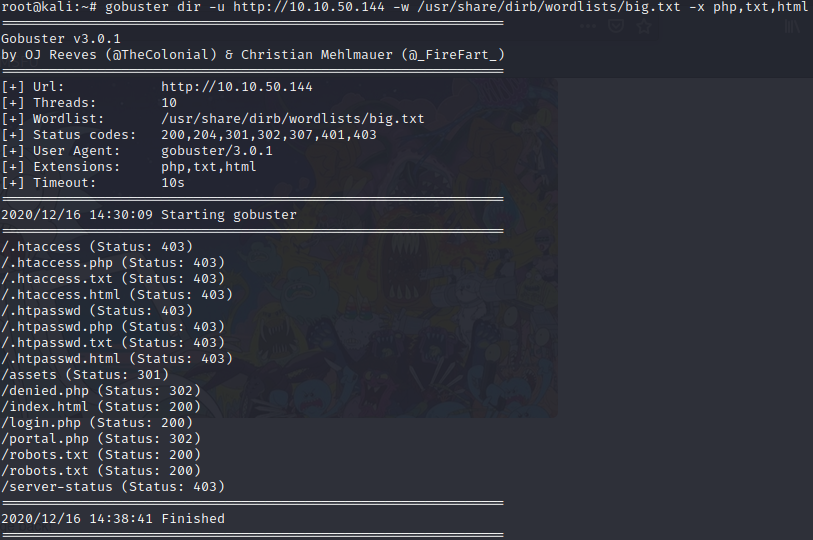
We have some interesting pages in this results. Let’s visit them.
Nothing seems to be out of the ordinary here.
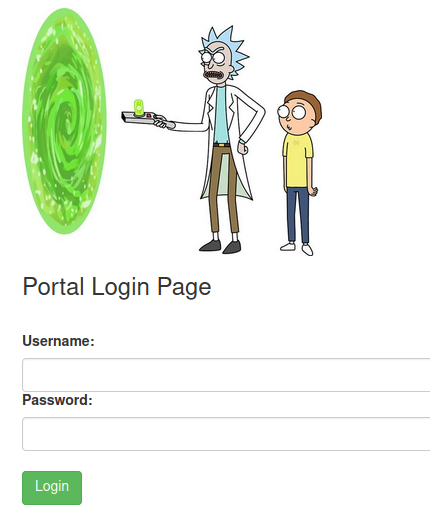
We have a possible username but no password yet.
In the robots.txt page we find a word. We try to login with the previously found username and this word as password, access is granted to a Command Panel
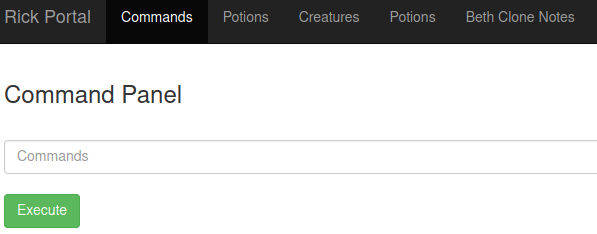
The links Potions, Creatures, and Beth Clone redirect to a /denied.php page where we can see Pickle Rick.
Exploitation
Let’s see if we can execute commands in this panel, first we try ls
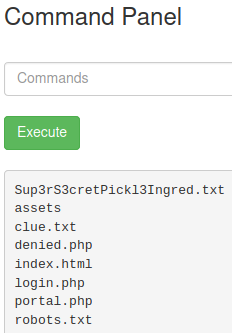
The first file seems promising, we try to open it with the command cat 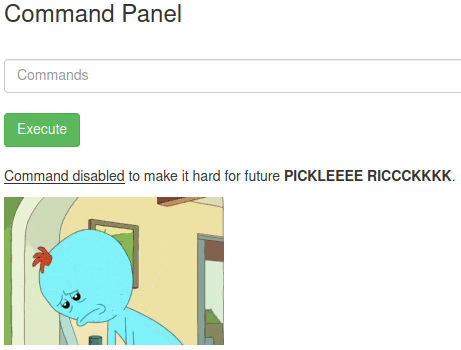
The command is disabled. We try with the command less
We got our first ingredient.
Then we use less to read the content of the clue.txt file, and it says, Look around the file system for the other ingredient.
Now, to see the directory we are in the system we use pwd
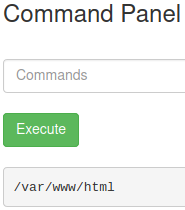
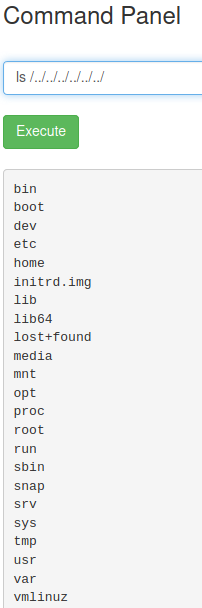
Then we list the root directory
the home directory has two subfolders, we list the one named rick, inside there is a file with the name second ingredients. We use less to view the content
If we try to list the /root directory the command doesn’t work. Let’s verify the permissions for that folder
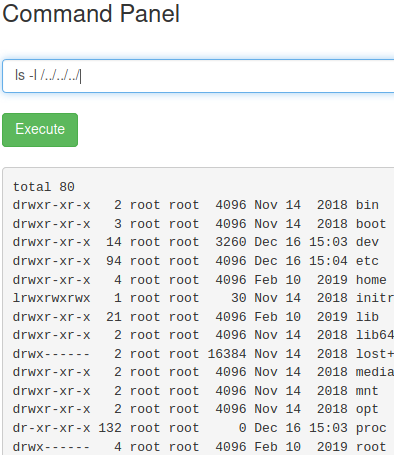
As expected, we don’t have the permissions to access that directory. To check what commands we can issue as ´root´ we can use sudo -l
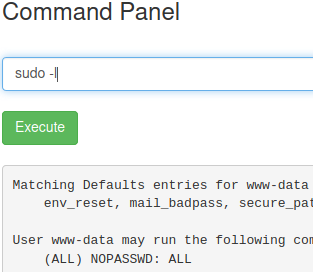
We have full access!! Let’s see what’s in the /root directory
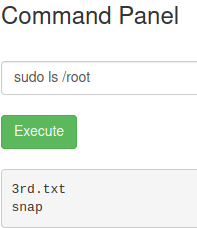
With less we see the content of the 3rd.txt file
That’s all, we have the three ingredients needed to turn Rick back into his human form.
